-
StatusOngoing
-
Status date2022-04-28
-
Activity Code7A.069
Tisalabs is an IoT company focused on the management challenges of the IoT industry. As the IoT industry matures the focus is moving from acquiring sensor data to providing security for the sensor network, geo-location of the sensors and the transmission of IoT data to secured repositories.
Tisalabs provides this essential IoT management infrastructure for enterprise customers through a cloud system linked with satellite communication for geographically dispersed IoT devices. The SecureSat project enhances our current system by improving the end-to-end security with a web solution managing the IoT devices and communications.
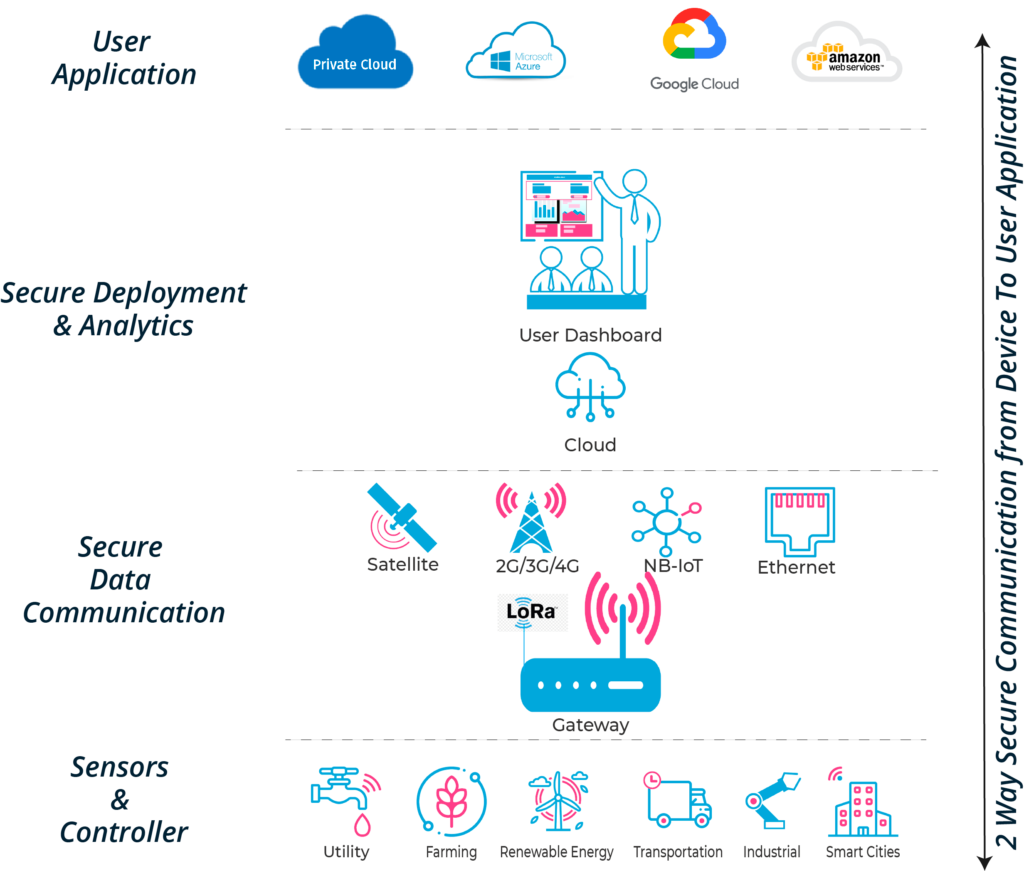
The objectives of the proposed activity are to develop and test a software solution enabling very secure communications between the IoT-enabled devices, gateway and the cloud data centre using a security framework with encrypted communications. This software will cover 4 main objectives:
-
Develop a solution with secure device identification with a secured identity key to identify each device.
-
Develop a solution that offers secure communication between IoT end node device, gateway and cloud data centre
-
Develop a solution with Signed firmware to improve the firmware integrity during the installation and upgrade in the devices
-
Develop a web application to facilitate the management of IoT devices and messages storage.
The purpose of the project is to develop a turnkey solution for customers to deploy Satellite enabled IoT Solutions with LoRa/LoRaWAN and strong Security using hardware keys. The following are the main challenges to building such a solution:
-
LoRa/LoRaWAN traffic to be available to customer even without an internet connection
-
Maintaining a unique identity for devices and their corresponding H/W keys securely.
-
Maintaining data consistency over the whole chain from device all the way to the user application, assuming a high latency connection.
-
Maintaining data custody over different cloud providers and hardwares.
To protect “Critical IoT infrastructure” IoT data must be 100% secure, 100% tamper proof and the identity of devices providing data must be 100% secure the proposed project is hardware agnostic and adapts to existing customer infrastructures.. Failure to protect IoT devices and IoT data leads to attacks and failure of critical infrastructure. The project
The Tisalabs SecureSat project is designed to allow customers to solve these pain points:
-
Financial: "IoT failure causes infrastructure failure"
-
Tisalabs integrates with standard IoT devices to provide identity management (only approved devices can join the IoT network), encryption of IoT data and integrity checking of the IoT data.
-
Cost of securing the data communication requires installing a VPN for each device in the field which is costly, our solution does not require a dedicated VPN.
-
-
Productivity: "Can’t manage what you don’t measure"
-
With poor visibility of the IoT resources it is very hard to plan and manage services at scale.
-
We provide our customers with a real-time view of their resources and their utilisation as well as updated billing information.
-
Scaling
-
-
Manage large scale IoT networks:
-
From a single dashboard manage remote and inaccessible IoT devices over multiple protocols with ease with unique Tisalabs features such as:
-
Managing security Keys
-
Firmware upgrades
-
Vulnerability signatures and threat databases
-
-
Data Validity based on EO data.
-
-
Process: When a device is compromised it is very late at that stage to do anything except damage control.
-
Support:
-
Reduce support costs
-
Our solution is resilient to failures with no single point of failure architecture.
-
The cost of efficiently managing a large number of IoT devices is increasingly expensive as it requires dedicated teams.
-
The SecureSat project in combination with the Tisalabs Tisacloud IoT platform enables customers to build state of the art secure critical IoT infrastructure solutions in their Digital transformation journey by providing them with the following features and associated benefits:
-
End-to-End Security: Your data is secure with best in class encryption tools managed using your own keys, stored in your private vault.
-
Identity Management: Each Device is identified by a Hardware Tamper proof TPM key, which identifies the device uniquely and correctly.
-
Automatic Deployment At Scale: Deploy software and firmware to 1000s of devices with a click of a button.
-
Secure Edge Computing Gateway: Edge gateway packed with multiple communication protocols from satellite, 4G/3G/2G to WiFi and more, provides a fast and secure delivery of your information to your applications.
-
Location Based: Location based tracking allows you to build geo-fencing activity for your devices, while providing you with in-dashboard status of your assets.
-
Single Pane Dashboard: Build rich dashboards to get insight into your data, with customized views including alerts and events.
-
AI based Intrusion Detection: Built in Intrusion Detection in edge gateway devices to protect against unauthorised or malicious access. During the project we will limit the scope at scope at facilitating the integration of the AI IDS onto the gateway.
The system allows for the easy and secure implementation of LoRa and LoRaWAN sensor data to be routed from end-devices to edge gateways all the way to the tisalabs Tisa-Cloud infrastructure, the data is received either from Satellite operator when using short burst messages which are limited in size providing the same Quality of Service with different communication technologies. as it stands the solution is built to provide the following key user features:
-
A secure space edge gateway that allows LoRa traffic to be routed through Satellite Short Burst Modems i.e IDP modems.
-
A secure process that allows IoT devices to be identified with a secured identity key to its gateway device, thereby providing secure encrypted communications between device and gateway.
-
Manage at-scale large number of IoT devices over a very wide geographical spread with differing communications infrastructure such as urban, rural and isolated.
-
A Secure encrypted communication between IoT end node device, gateway and cloud data centre even when using Satellite communications.
-
A signed firmware to improve the firmware integrity during the installation and upgrade in the gateway and end devices with minimal data exchange.
-
A web application to facilitate the management of IoT devices and storage of messages as well as maintaining a consistent and automatic firmware and software upgrades.
-
A web application to monitor device security and vulnerabilities whilst providing devices status information.
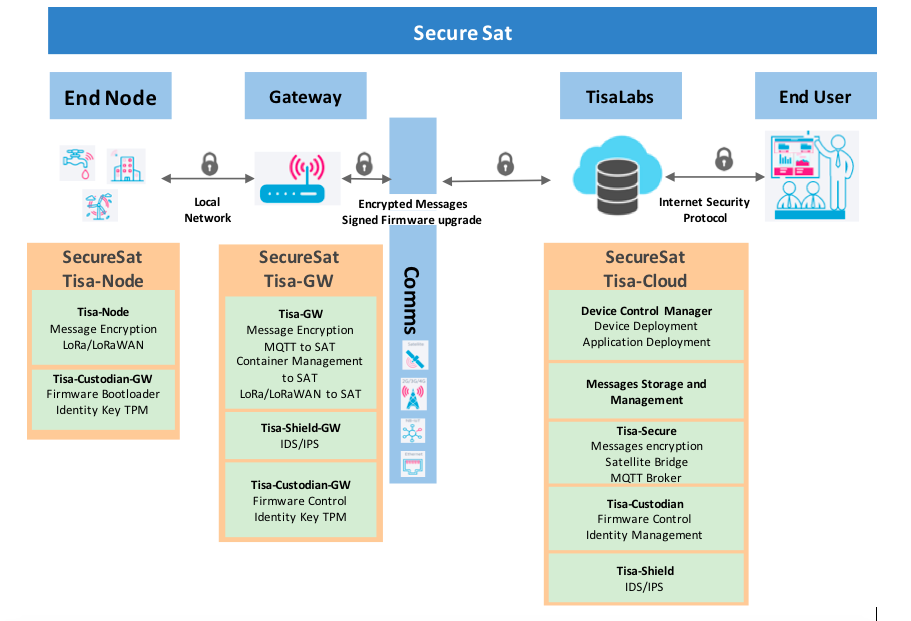
The functional diagram in the figure below shows the main system functionalities in each of the main system components involved
The project plan includes 5 work packages divided in 3 phases and 6 milestones.
-
Phase 1: Requirements and Design. In this phase a concise user needs and requirements assessment is performed before defining the system requirements and a comprehensive system design. The outputs are reviewed in the PDR-CDR milestone.
-
Phase 2: Development, Integration and Testing. This phase includes the Development of the system, integration of the components and functional testing (Factory Acceptance Test).
-
Phase 3: System Validation and Project Closure. In this phase full system validation is performed.
Further to the ESA project completion the system will be made available to a select beta customers for customer validation and feedback.
The project is at the first phase of design specifications. We have completed all the technology choices and have reviewed and completed all of the technical challenges with the project.
We are now engaging in the product development phase which is starting now and will run for the next 6 month which allows us to develop the product as discussed and reviewed with qualified customers.



