
-
StatusCompleted
-
Status date2023-02-08
-
Activity Code6A.079
There are three EGSE platforms being evaluated: RF SCOE, Power SCOE and Instrument SCOE. The existing platforms will undergo a deep architectural re-evaluation with the goal of identifying vulnerabilities that allow an unauthorized actor to take control of the system thus threatening the mission. Such threats could lead to extensive downtimes, loss of data or even damage to the satellite.
The ISO, NIST and IEC standards will be taken as a baseline guide to implement the necessary measures on an administrative, physical and software level. Finally, each EGSE will be audited against these standards.
The biggest challenge at all is that this industry is well established and has a long history without the need for severe security requirements because EGSE were operated offline, completely cut from the internet. Since remote operation is shifting towards distributed sites, the cybersecurity aspects become more prevalent. Many long-established remote protocols like SCPI or simple telnet, and even the satellite protocols PUS/EDEN are agnostic to whoever emitted the commands. Making these protocols “safe” could have the impact of setting new standards across the EGSE industry.
The cybersecure EGSE will be hardened according to the CIS benchmark which will prevent inside and outside intruders, as well as online and offline attacks from easily comprising the system. “Easily” in the sense that no system is perfect and zero-day attacks can never be out ruled, but at least the time it takes can be prolonged. And this might be already sufficient since the EGSE will continuously being monitored for indicators of compromise (IOC) thus quick preventive measures can be taken.
Securing the remote protocols not only have the benefit of being unusable by packet sniffers, but also avoids human errors if the receiver validates the origin of the source packet. Human errors, especially accidental misconfiguration is still a downtime factor in the EGSE world.
-
CIS benchmark hardened operating system
-
Remote client and server validation and authentication
-
Traffic encryption
-
Continuous security platform monitoring
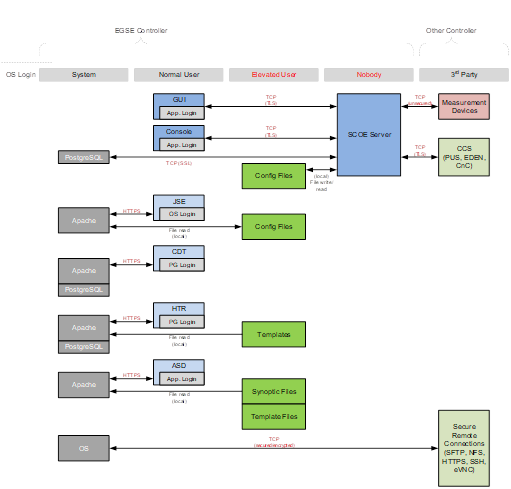
The EGSE platform is running a Linux operating system with the main service workhorse running as unprivileged user. The main service accepts remote connections from a central checkout system (CCS) using the PUS protocol. Graphical front ends like reporting, synoptic and configuration are instantiated as the current logged-in user and connect to various services. Instead of plain text, all remote interfaces use client-server authentication and data encryption like TLS, SSL and HTTPS. Configuration and template files are being protected by user and password control.
High Level Project Plan with milestones (MS) and work-packages (WP)
KO Kick-off Meeting
Definition Phase:
MS1: RR Requirements Review
Technology Phase:
MS2: PDR Preliminary Design Review
Product Phase:
MS3: CDR Critical Design Review
MS4: TRR Test Readiness Review
MS5: FS Final Review
Definition Phase
WP1001 Project Management & Quality Assurance
WP2100 Definition Power/Instrument SCOE
WP2200 Definition RF SCOE
Technology Phase
WP1002 Project Management & Quality Assurance
WP3100 Technology Power/Instrument SCOE
WP3200 Technology RF SCOE
Product Phase
WP1003 Project Management & Quality Assurance
WP4100 Product Power/Instrument SCOE
WP4200 Product RF SCOE
Project is in Product Phase and test is finished and documentation for final review was provided. The final review documentation is currently in review at ESA.



